Data Privacy Engineering
Demand a new standard in data privacy by applying data privacy engineering principles at the outset of applications architecture. Using the Sertainty Data Privacy Platform, Transformations, Inc’s Uluro with uSecure solution empowers data to assure data privacy even while under process.
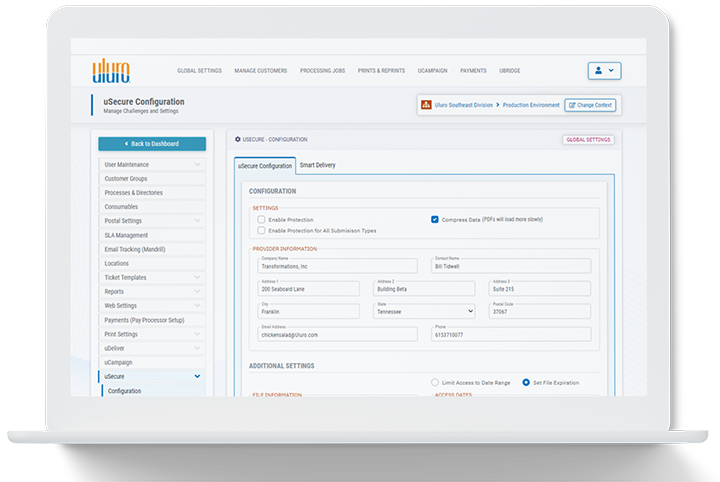
uSecure Data Composition Solution
uSecure is Privacy Proven
No matter the highly regulated or customer communications management industry your business falls into, your risk is minimized when your confidential data remains secure and compliant – at-rest, in-transit, under-process. Uluro with uSecure is the composition tool that sets a new standard for protection and control.
All other data composition tools have decentralized privacy controls, which may leave data exposed, but Uluro with uSecure maintains governance and protection within the data itself, even while in use. The selective decryption process allows data centers to maintain data protection even in an operational environment. Even when an operator (or applications) accesses part of the file, the other parts remain cloaked and private.
It’s time to demand a higher level of privacy from your data center – a level you can only get with uSecure.
uSecure Selective Decryption in Use
uSecure enables the selective decryption that helps protect data at any point in its lifecyle – from the data center to the end users in financial and other highly-regulated industries. The technology maintains a level of protection that cannot be found in any other composition tool, making uSecure essential for any business in customer communications management.

Finance and Insurance
Essential information can be accessed in the file even while PII and sensitive data maintains its privacy and tracks its use.

Healthcare
Data centers use uSecure to protect sensitive HIPAA information while maintaining efficient data use.

Government
Local and state governments share and use data with public and private data centers with the confidence that personal data and other sensitive information remains secure.

Utilities
Operators selectively decrypt only the information needed for use and the rest remains secure.

“One of the big things in our industry is data security, so whether we’re working in the healthcare industry, insurance industry, even utilities in some cases, that’s one of the first things [our customers] go to ‘what do you all do for data security?’ When you introduce uSecure and uProtect products into the mix, you can almost see the relief on [the customer’s] side. Now, when we talk to particular industries, we have started requiring the use of uSecure. That’s how strongly we feel about the product.”

John Young
Director of Operations at Bluegrass Integrated Solutions
Set Your Own Rules for Data Ownership

uProtect
Set rules that govern your data throughout its entire lifecycle. With the uProtect feature of uSecure, you take control of your data with policy-based rules you can set before sending to the data center. The data maintains rules and policies – actively protecting itself at every touchpoint.
Featured Resources
2021 Tag Cyber Annual
Market Outlooks and Industry Insights Read pages 15 and 261-264 in the 2021 Handbook & Reference Guide published by Tag Cyber
Transformations, Inc. Success Story
Read here about the success of Transformation Inc. Discover how Sertainty enabled Transformations, Inc. to develop a solution that keeps data secure.
Contact Us
To learn more about uSecure and how it uses the Sertainty technology to revolutionize data protection and control, please fill out the form below.