Owner-Controlled & Policy-Driven
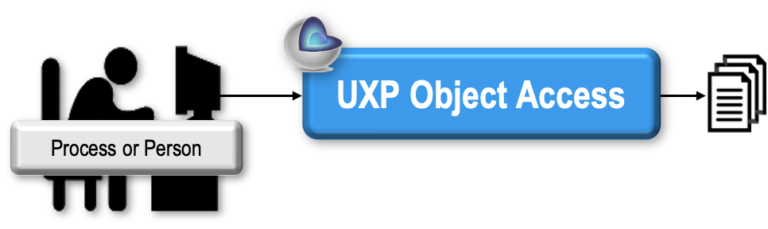
UXP Object access requires proximity to UXP Technology. Authentication for the human, machine or process must successfully occur before UXP Object access is granted. The UXP Intelligence controls this process.
UXP Object Access Components
UXP Object access requires the following the components:
- UXP Object
- KCL Code
- UXP Engine
- P-code Execution Engine
- Environment Scanner
- Libraries
- Configurations
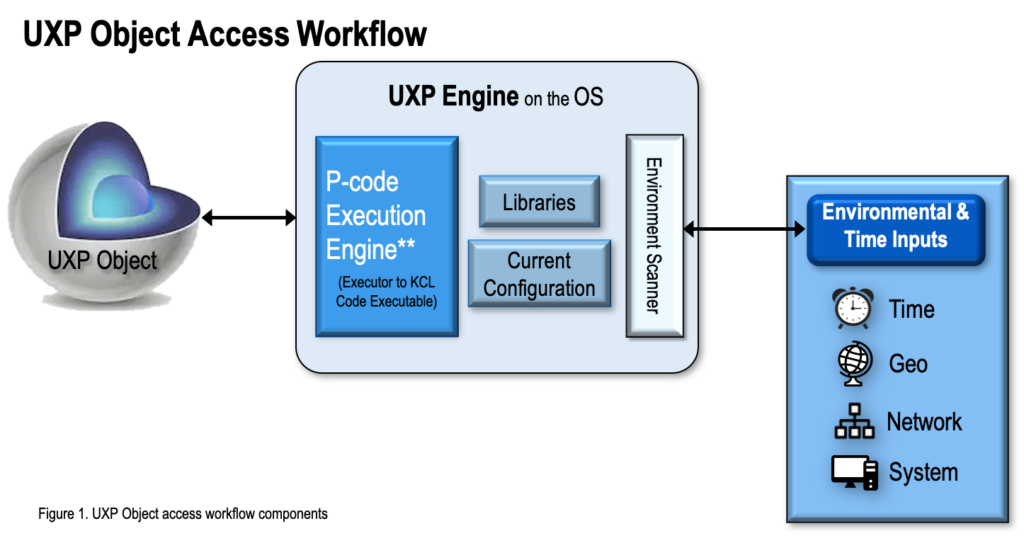
UXP Object
The KCL Code is the intelligence that maintains control of the UXP Object on behalf the data owner.
The KCL Code does the following:
- Communicates directly with the P-code Execution Engine
- Makes recommendations to the P-code Execution Engine for the following:
- Challenge Pair for presentment
- Access and Mitigation policies for evaluation
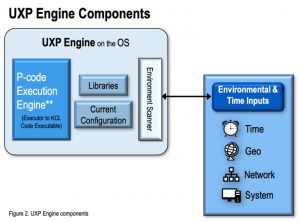
UXP Engine
The UXP Engine plays an overall central role in UXP Technology. For UXP Object access, the UXP Engine participates in the authentication cycle and in the Object’s management once the Object is successfully accessed.

Libraries
The UXP Engine Libraries manage a UXP Object’s initial validation as well as the communication channel with the User attempting access.
The Libraries are responsible for the following:
- Validating the UXP Object
- Establishing the communication channel between the UXP Object and the P-code Execution Engine (details discussed below in the P-code Execution Engine section)
- Presenting the individual Prompts to the User
- Managing the UXP Object’s access after a successful authentication
- Continuing to communicate with the P-code Engine as needed while Object is active
P-code Execution Engine
The P-code Execution Engine is the executor between the UXP Object and the UXP Engine.
The P-code Execution Engine is responsible for the following:
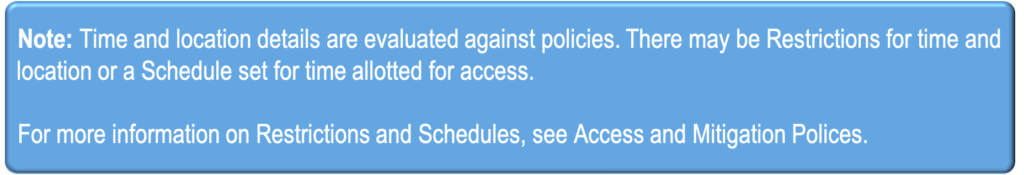
- Establishing initial trust of the UXP Object using information from the Environment Scanner
- Time
- Location
- Communicating with the KCL Code in the UXP Object
- Recommending Access and Mitigation policies to the UXP Engine for execution
- Confirming the validity of the User Responses to the UXP Engine
Environment Scanner
The Environment Scanner communicates with an external server to capture time and location information.
The Scanner collects the information below:
- Current time from an external server process
- Current location of the UXP Object
Additionally while the UXP Object is active, the Scanner periodically updates time and location of the UXP Object.
UXP Object Access Process
UXP Object access requires proximity to the UXP Technology Libraries. If the either the Object is not proximal to the UXP Technology or the Object is deemed invalid, the Object will remain inert.
The UXP Object access process consists of several parallel actions. The actions are based on the recommendations (User Definition components) from the KCL Code communicated to the P-code Execution Engine. The P-code Engine serves as the executor for the UXP Object. The P-code Engine passes the recommendations to the UXP Engine that executes them without deviation.
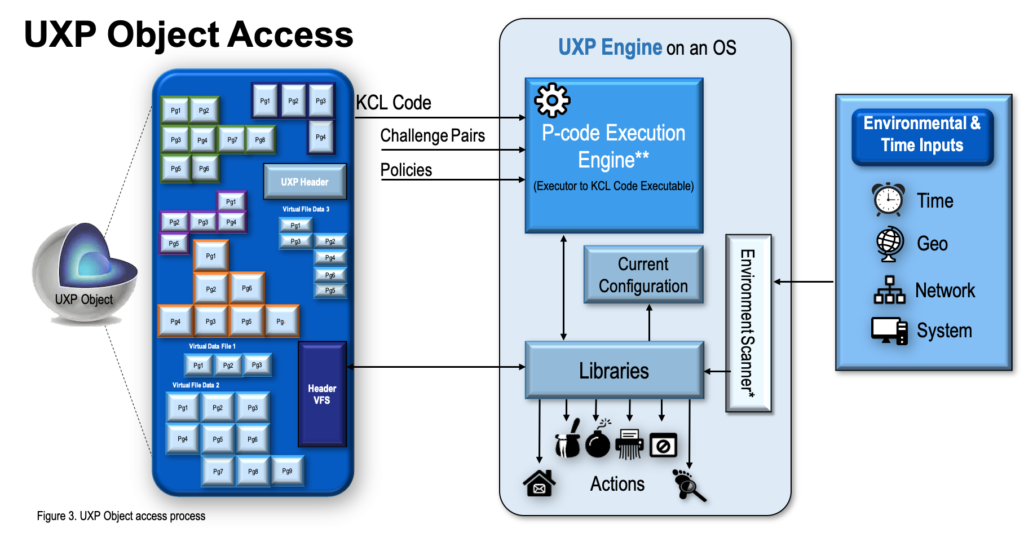
Object Access Activities
- The UXP Engine evaluates the UXP header in the UXP Object to validate Object legitimacy.
- The UXP Engine passes control to the P-Code Execution Engine to facilitate the authentication cycle.
- The P-code Engine communicates directly with the KCL Code in the UXP Object.
- The UXP Engine requests data from Environment Scanner.
- The Environment Scanner requests data from the external server’s time/location process.
- The P-code Engine evaluates the time/location information with the provided policies.
- The authentication cycle below repeats until access is granted or denied.
- The KCL Code recommend access and mitigation policies, or actions, to the P-Code Engine.
- The P-code Engine communicates with the UXP Engine the “next” recommended policy execution that may or may not include additional Prompts presented.
- The UXP Engine executes the recommended action and/or presents the recommended Prompt.
- If a Prompt is presented, the UXP Engine confirms with P-code Engine the Response accuracy.
- Upon successful access, the UXP Engine takes control of the active session for the UXP Object.
- The UXP Engine periodically requests a time and location update from the Environment Scanner. The UXP Engine communicates with the P-code Engine for potential policy execution based on time and/or location.